Overview
With the release of iOS 9, Apple introduced a new feature called App Transport Security (ATS) which enforces secure connections between an app and web services. In the near future, all apps in the app store will be required to have ATS enabled unless you provide reasonable justification for ATS exceptions, as part of the app review process.
ATS restrictions apply to applications that target iOS 9.0 and later. Existing apps in the app store will not be affected, but you will need to apply ATS restrictions when you publish new apps or update your existing apps.
The Brightcove ecosystem supports ATS restrictions. In most cases, you should build your apps with ATS enabled. If you have a need to connect to non-secure URLs, then you can submit your ATS exceptions along with justification to Apple's App Store review.
Choose either:
As a last resort, you can disable ATS requirements. Keep in mind that this option will be going away soon.
Building Apps with ATS Enabled
If you use secure connections over HTTPS between your app and web services, then you can enable App Transport Security for your app.
To build you apps with ATS enabled, do the following:
- Enable your CDN for secure communication.
-
Video Cloud customers (whether you are using the house CDN or a named CDN) should contact their Brightcove account managers to ensure accounts are configured to deliver over HTTPS.
-
For those using remote assets, you may need to configure your CDN appropriately.
-
-
Use secure communication to deliver your media content. This includes video, ads, captions, poster images, thumbnails and other third-party API connections.
-
Video Cloud customers: Use the Playback API to retrieve the secure protocol for each of your assets.
-
Brightcove Player customers: Make sure your media content is delivered over HTTPS.
-
Using ATS exceptions
If you need to use non-secure connections between your app and web services, then you can try using ATS exceptions. Keep in mind that the reason for ATS requirements is to ensure users have a good level of security when using your app. So, make sure that your app cannot use secure connections before digging into ATS exceptions.
There are specific keys that you can use to bypass ATS requirements. These exceptions will trigger an additional App Store review and will require that you provide reasonable justification. For details, see the App Store Review for ATS document.
Note that you may be able to get a justification for an exception for content that is already encrypted (ie. FairPlay), but keep in mind that It is best practice to use HTTPS when possible.
Disabling ATS requirements
When building applications that target the iOS 9 SDK or later, you may choose to disable ATS. Follow these steps to disable ATS requirements in your app:
-
In Xcode, right click on the Info.plist file and open it as Source Code.
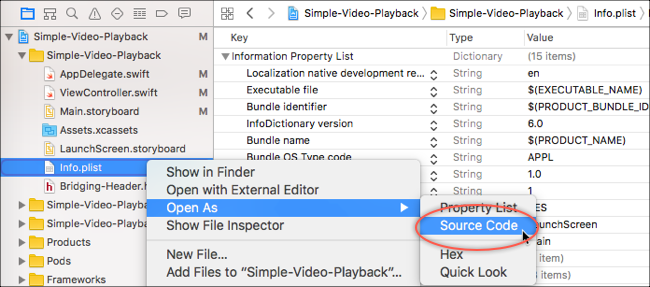
Source code info.plist -
Copy the following code:
<key>NSAppTransportSecurity</key> <dict> <key>NSAllowsArbitraryLoads</key> <true/> </dict> -
In the Info.plist file, before the closing
</dict>tag, paste the code from above.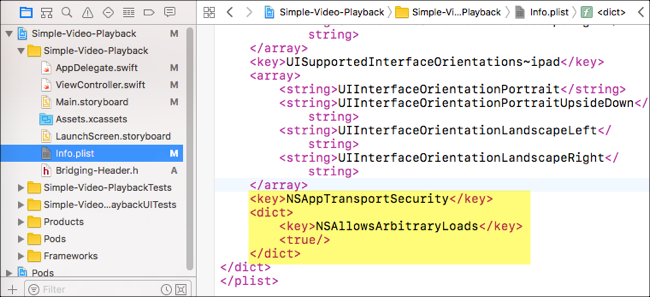
Allow arbitrary loads -
In Xcode, when you open the Info.plist file as Property List, you should now see this entry in the plist dictionary.
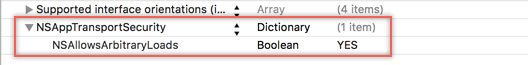
ATS disabled
Disabling ATS does not alter existing HTTPS connections. It simply prevents iOS from enforcing additional security requirements on your http communication.
Additional Resources
- Apple Developer Forum: App Transport Security Required January 2017
- Apple Developer Forum: App Transport Security update
